When yesterday from the territory of Ukraine across Europe suddenly began to spread the virus-the extortioner, the blocking network of companies, government agencies and critical infrastructure, at first thought it was just another hacking program aimed at making a profit — even if it is particularly malicious. But the fact that the virus spreads from the territory of Ukraine, raises more serious questions. Because the hacker underground there are cyberwar for many years — and, it seems, they do so at the behest of Russia.
As details of the attack, the representatives of Ukrainian companies working in the field of cybersecurity, and government agencies claim that the hackers behind this virus-the extortioner called Petya (also known as NotPetya or Nyetya) — it’s not just thieves. Rather, they attributed the attacks to political leaders, seeking again to wreak havoc and destroy the Ukrainian institutions using powerful virus ransomware to hide their true motives. The same conclusion was reached by some Western analysts-experts in the field of cybersecurity, studying Petya rampant virus and tracking its spread.
Focused approach
On Tuesday morning the Ukrainian media first began extensive coverage of the situation related to the spread of the virus Petya, the attack which was subjected to such objects, as the Ukrainian banks, Kyiv Borispol airport, as well as power company “Kyivenergo” and “Ukrenergo”.
Victims of the virus Petya steel and many other objects. Among the victims — the Danish shipping company Maersk, the Russian oil company “Rosneft” and even the American pharmaceutical giant Merck. However, Ukrainian analysts on cyber security believe that the main goal is Ukraine. Outbreak Petya is just another blow in their eternal cyber war with organized and ruthless hackers who openly declare the Ukrainian authorities connected with Russian government agencies. “I think that it was directed against us, — says Roman Boyarchuk, head of the Centre for cyber defence and combating cyber threats, divisions of Public service of special communication and information protection of Ukraine. — That’s right — not the work of criminals. Most likely, the attack is the state.”
On the question of whether the state-sponsored Russia, Boyarchuk added: “it’s Hard to imagine that someone else wanted to do it”.
Boyarchuk indicates the time of the attack. The virus attacked on the eve of the Constitution day of Ukraine, which celebrates its independence after the collapse of the Soviet Union. On Tuesday, the Ukraine has become a victim and even deliberate act of physical violence, when the explosion of a car bomb in Kiev killed an employee of the Main intelligence Directorate of the Ministry of defense of Ukraine.
According to some Ukrainian analysts in the field of security, confirmation of this theory are evidence of a more technical properties. Kiev company Information Systems Security Partners (ISSP) is responsible for security of information systems and was the first to take protective measures during the last few series of cyber attacks on Ukrainian enterprises and government agencies. According to her representative, the company’s specialists have found evidence that professional hackers have quietly penetrated the network at least some of the Ukrainian objects for two or three months before, was launched virus-extortionist, which paralyzed the work of these organizations.
“In accordance with the intermediate data obtained as a result of our analysis, our analysts came to the conclusion that the destructive impact on the infrastructure of the studied organizations was carried out using [ransomware]. But it was done and with the direct participation of intruding into a network of criminals who already some time were in infrastructure,” he wrote in an email edition of WIRED, the judicial expert, Alex. To provide more detailed information about the evidence of these long incursions of the company ISSP refused but, according to her representative, the methods used by hackers, similar to those used in the previous attacks committed in 2015 and 2016. President of Ukraine Petro Poroshenko called the break-ins are acts of aggression under the “cyber war” waged by the Russian security services and military intelligence. Jasinski declined to name the victims of the virus Petya organizations, the networks which were discovered traces of the criminals. But he notes that they have one of the largest Ukrainian banks and the company relating to critical infrastructure.
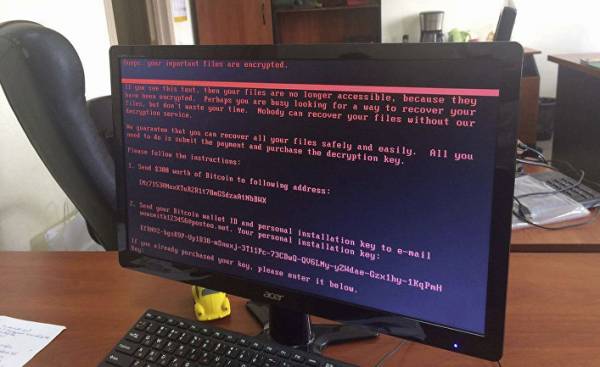
According to the representative of the company ISSP, their experts also found that the virus Petya acts not only as virus-extortionist. It not simply encrypts the infected hard disk requires a decryption key $ 300 in bitcoins. In some cases, it just erased the data in the computers on the same network, removing from the infected computer, inside of the system “master boot record”. It contains information about how to load its operating system. Jasinski argues that, judging by the behavior of attackers, they actually tried to extort money from their victims, and wanted to inflict maximum damage to the system. As suggested by Jasinski, hackers might still try to “remove traces” of previous operations to deprive the investigators of the ability to fully assess the scale of their penetration, trying to completely remove data from attacked networks.
Deletion of the computer’s master boot record is also the hallmark of a group of cybercriminals known among cybersecurity experts as Sandworm that has plagued Ukraine for several years. Starting from October 2015 until the end of last year the group attacked the network of the Ukrainian media, transport infrastructure and government ministries and departments. She twice called blackouts, attacking the power system of Ukraine. Specialists of the company FireEye, working in the field of cyber security believe that these criminals are connected with Russia.
They base their conclusion on the results of the study publicly available command and control server used by the attackers. On the server there are documents in the Russian language, explaining how to use the malware, which the attackers installed on the interested in their computers.
Unusual criminals
To confirm the theory that the virus Petya specifically targeting Ukraine, yet failed. Besides, this theory does not explain sufficiently why the malicious program have spread so far outside Ukraine, causing damage and Russian objects.
However, not only Ukrainians are inclined in the direction of the hypothesis, according to which the virus Petya was created not as a way of making money, but as a tool for use in the campaign, funded by government and directed against Ukraine. According to Symantec, as of Tuesday morning (in the US) more than 60% of their registered cases of infection with this virus occurred in Ukraine, and this means that the attack likely started there. Cyber security analysts on Tuesday found that in many cases the infection occurred through Petya update file Ukrainian applications accounting software MeDoc. According to Craig Williams (Craig Williams), the head of the analytical group of the company Talos (Cisco units, engaged in the exploration and analysis of threats to information security — approx. TRANS.), companies doing tax accounting or interacting with Ukraine in the financial sector, MeDoc used quite widely. And some of this may be one reason for the proliferation of ransomware outside of Ukraine.
Applied tactic also indicates that the virus Petya “has a very clear idea of who he needs to influence enterprises and companies associated with the Ukrainian government,” Williams says. “It is obvious that this is a political signal,” he said.
Ukrainian police also noted that in addition to the software MeDoc the spread of the virus Petya contributed to a phishing email. This means careful selection of objects for infection by a virus-the extortioner, are not based on a random distribution of a worm, and the choice of language spoken by the victim. However, other analysts working in the field of cybersecurity, could not confirm these allegations.
Although the motives of cybercriminals remain unclear, many members of the community cyber security come to a common opinion, that in this case are not ordinary criminals. In addition to the trick with updating MeDoc virus Petya also distributed in the network using the various automated instruments using not quite understand the protocols like Microsoft windows management instrumentation, PSExec and server message block SMB, which are characterized by high level of complexity. However, criminals have shown a remarkable indifference to the monetary component of this malware. To communicate with victims of the virus they used a built-in bitcoin address, which is easy to track and the email address that was “deleted” by the owner within 12 hours after the attack began. Partly so with the new version of the virus Petya cybercriminals earned a paltry sum of 10 thousand dollars.
This disagreement suggests that they had an ulterior motive, says Nick weaver (Nick Weaver), an analyst in the field of computer security International computer science Institute in Berkeley. “It seems that under the guise of a virus-the extortioner was developed malicious program designed to bring systems down, says weaver. Any time they inexplicably just blundered with extortion. Or real target is the failure of the devices, and this was done so that the effect is felt in Ukraine.”
All this leads to another idea (no matter how strange it may seem) that lock computers and the damage caused to the companies in different countries — from USA to Spain and even in Russia — is arguably the only “accidental loss” side effects. It is not excluded that in fact, hackers continue a protracted offensive in the Ukraine. But this time the pain feels and the rest of the world.







